Articles & Alerts
Zoom Security & Privacy: Protecting Your Virtual Meetings and Protecting Yourself
During these days of increased remote work, many in-person meetings and events are going virtual and videoconferencing platforms are becoming more necessary to our daily routines. As Zoom has become more popular, limitations and security issues are being identified within the platform. Under certain circumstances, Zoom can be exploited to steal credentials or launch applications on a target machine, leading to more severe issues. Researchers have found nearly 2,300 login credentials in a criminal online forum.
With a few recommended changes, you can make Zoom a more secure place to conduct business. The below recommendations can help you stay safe while using the platform:
1. Keep the Meeting ID private – Do not publish the link online unless absolutely necessary. Instead, send the link or meeting ID directly to trusted participants.
2. Keep the app up-to-date – Updates often address security and privacy concerns. Recent Zoom releases created defaults to waiting room and password creation for all meetings.
- Screen participants by turning on waiting room – With the waiting room option enabled, the host will be able to see each participant before allowing them to join. This option can limit disruptions or unexpected participants.
- Setting a meeting password – This option ensures that all users properly secure their meetings and can prevent unexpected participants from joining the meeting.
3. Utilize the security toolbar – The latest Zoom update on April 8, 2020 included a new feature – a “Security” icon that will allow hosts and co-hosts to take action quickly against security infractions. The menu includes “un/lock meeting” and “enable/disable waiting room.”
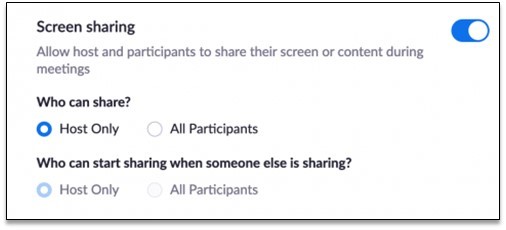
4. Disable participant screen sharing – This way, only the host(s) will be able to share their screens.
- To disable participant screen sharing, enter your Zoom account settings and look under In Meeting (Basic). Under the screen sharing header, you can restrict any screen sharing or limit screen sharing to HOST ONLY.
5. Use unique login credentials – It is very common for users to reuse login credentials across many platforms. Ensure that the email and password combination you are using for Zoom is not used for any other website or domain.
If you have any questions or concerns about Zoom and other web-based conferencing solutions, or IT security in general, please reach out to our team at Redpoint Cybersecurity at [email protected].